A common scenario that companies face is controlling the usage of the relational databases (RDS) that they have for development or testing environments. Stopping the RDS when it’s not being used can significantly lower the company’s AWS costs.
One of the ways to stop an RDS Instance is by using AWS Cloud Watch Events in conjunction with AWS Lambda Function written in Python 2.7.
In this example, we have RDS development databases that we need to stop every day at 10 PM EST.
Below are the four steps required to do this:
Step 1 – Create IAM Role/Policy: AWS Lambda will need to assume a role that has access to AWS services like RDS and Cloud Watch.
IAM Policy: First we need to create a new policy that we will attach to the IAM role later:
- From AWS console, choose IAM service and click on Policies
- Click on the “Create Policy” button
- Click on JSON Tab and use below JSON to allow access to some actions in RDS and Cloud Watch Logs Services
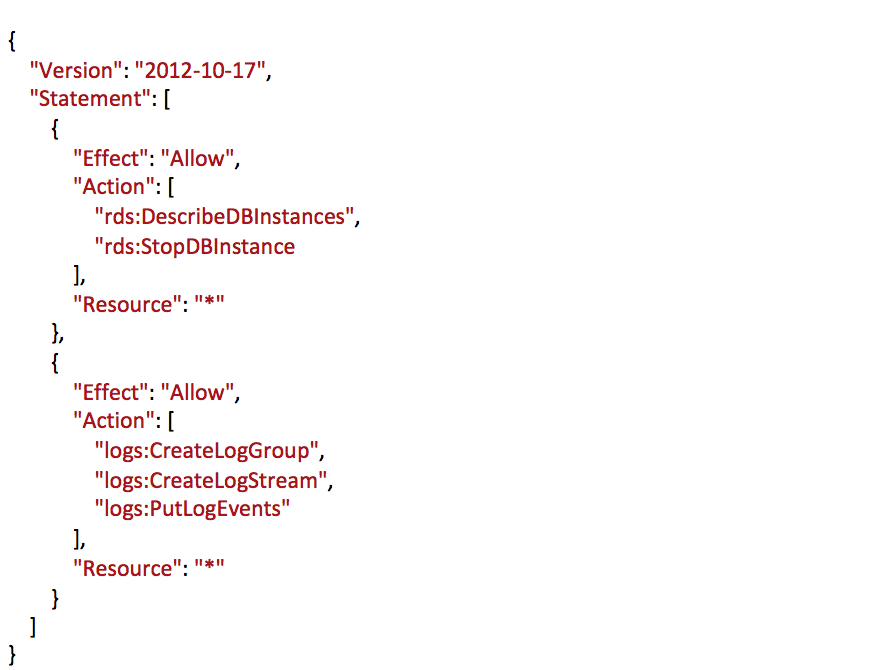
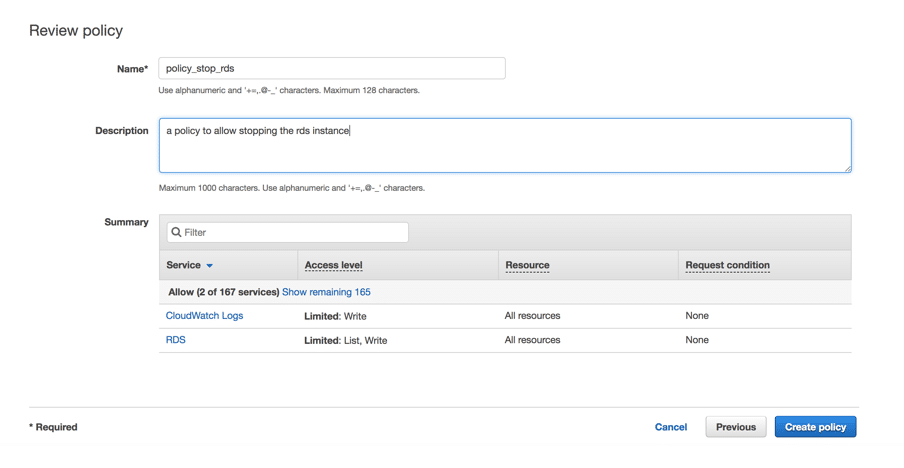
- Click on the “Review Policy” button.
- Provide a name for the policy “policy_stop_rds” and some description
- Click “Create Policy”
IAM Role:
- From AWS console, choose IAM service and click on Roles
- Click on “Create Role” button
- Choose “Lambda” as the service that will use the role and click “Next: Permissions”
- Search for the policy we created on previous steps “policy_stop_rds,” check it, and then click “Next: Tags”
- Add any tag key value pairs needed and then click “Next: Review”
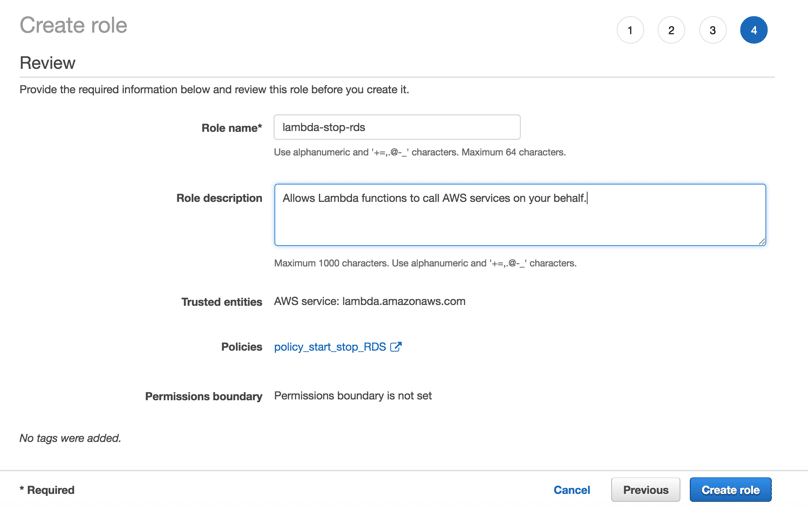
- Choose a Role name “lambda-stop-rds” and then click “Create role”
Step 2 – Create AWS Lambda Function:
- From AWS console, choose Lambda service. Make sure that you’re in the same region where your RDS resides
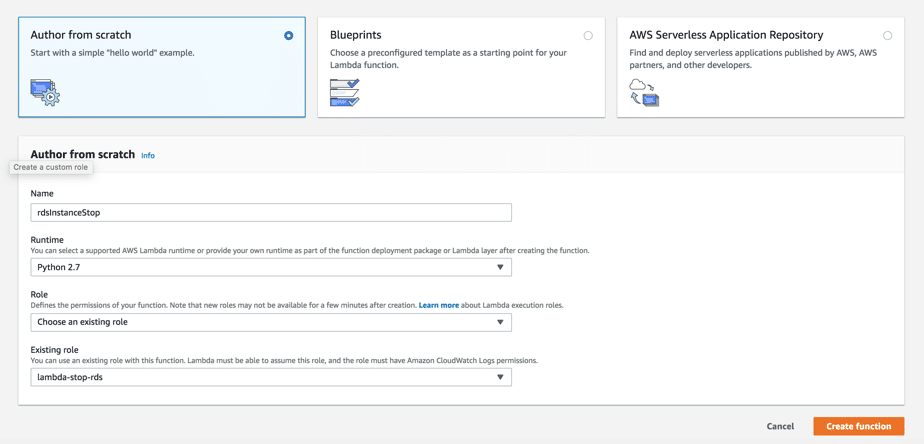
- Click on “Create Function” and choose “Author from scratch”.
- Name: rdsInstanceStop
- Runtime: choose python2.7
- Role: choose existing role “lambda-stop-rds”
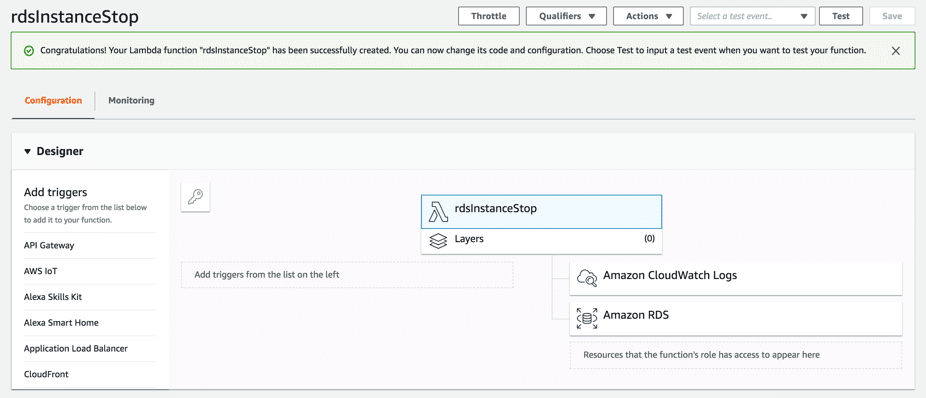
- The lambda function will be created, resulting in this page:
- In another tab, open the IAM role we created in previous steps “lambda-stop-rds”
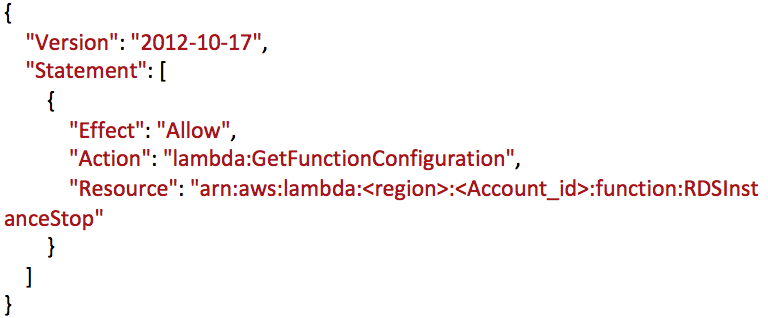
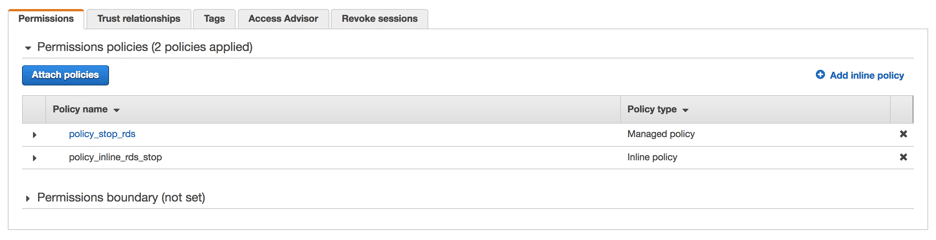
- Add the Lambda Function ARN to the inline policies in IAM role we created in first step (you can get this from Lambda Function page in the right top corner)
- Click on “add inline policy” and add the following JSON, replace the resource with the ARN from above step, and save the policy with name “policy_inline_stop_rds”
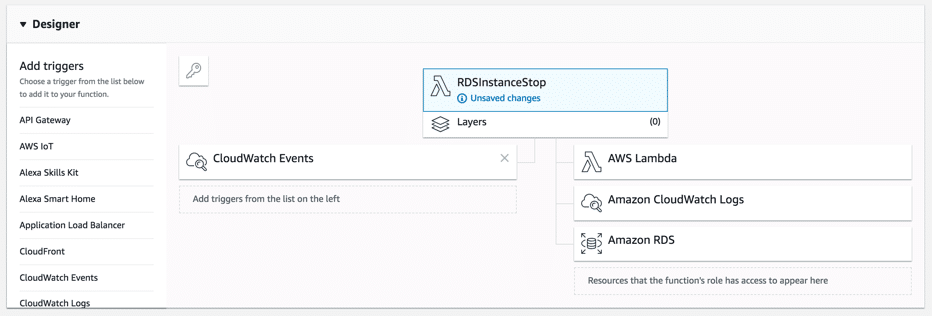
- Designer: From Lambda function page, make sure that resources section has “AWS lambda” added.
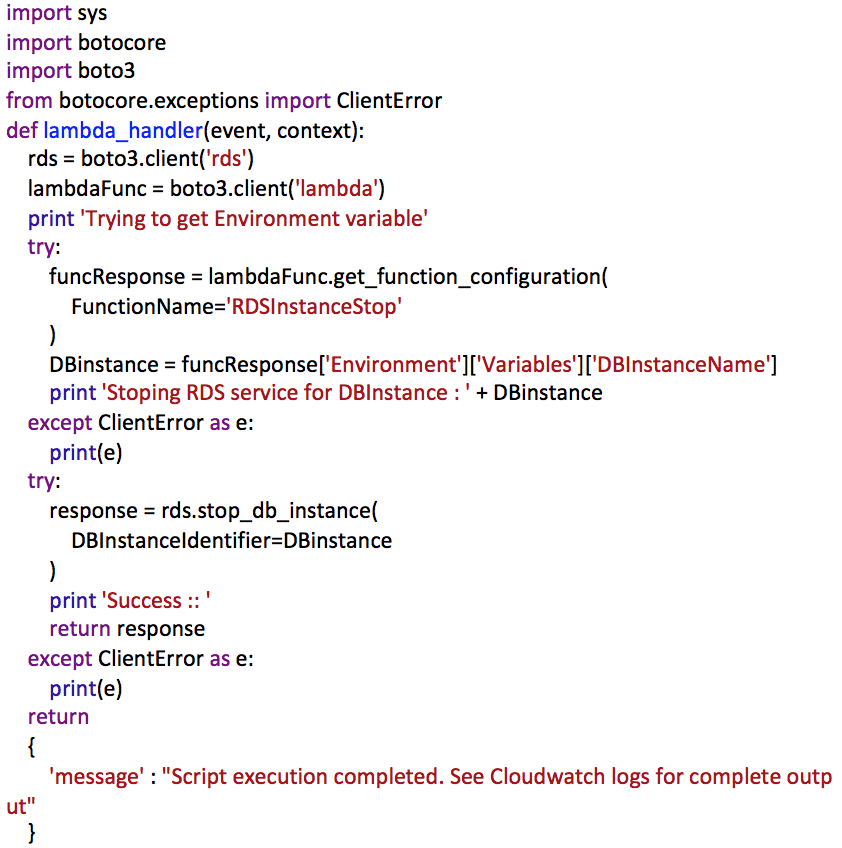
- Function Code: Add the following function code to the Lambda function:
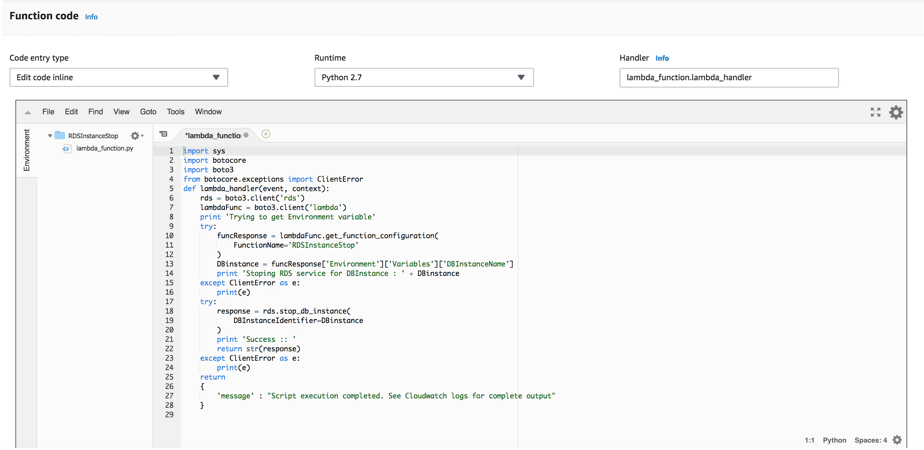
- Environment variables: To use this Lambda function in other environments, we used the environment variables to define the db instance name
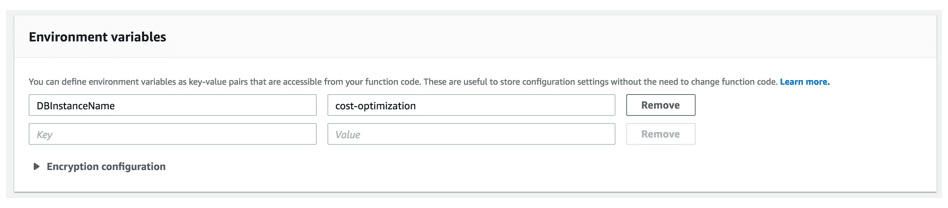
- Tags: Add a key value pairs of tags as needed
- Execution Role: use the existing execution role “lambda-stop-rds”
- Keep all other settings with default values
Step 3 – Test the Lambda function:
- On the top right corner of the screen select Testand Configure Test events
- Select Create New Test Eventand select the Hello World event template
- When you click Save, the execution should succeed
- If your DB is not started, there is nothing to stop and hence you will get an error message similar to “Instance <> is not in available state.”
Step 4 – Schedule the run of the Lambda function:
- From AWS console, choose Cloud Watch and click on Rules
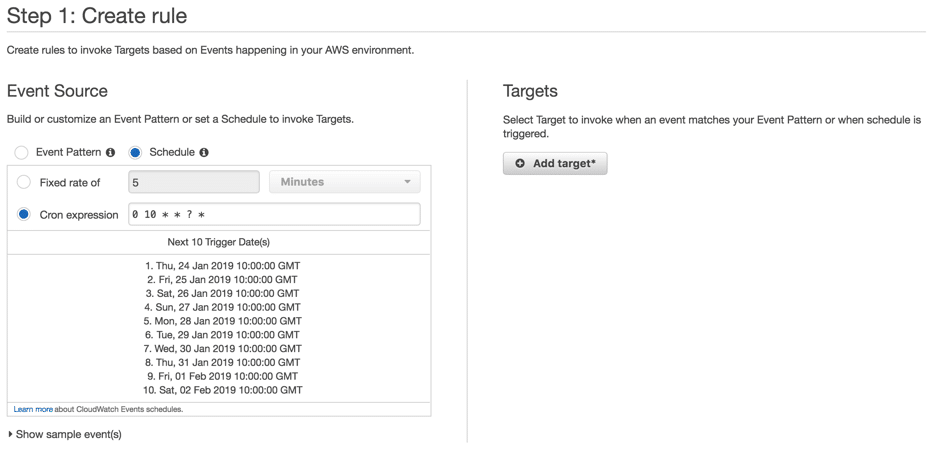
- Click on “Create rule”
- Choose “Schedule” and use cron expression “0 10 * * ? *” to run the event every day at 10 PM EST.
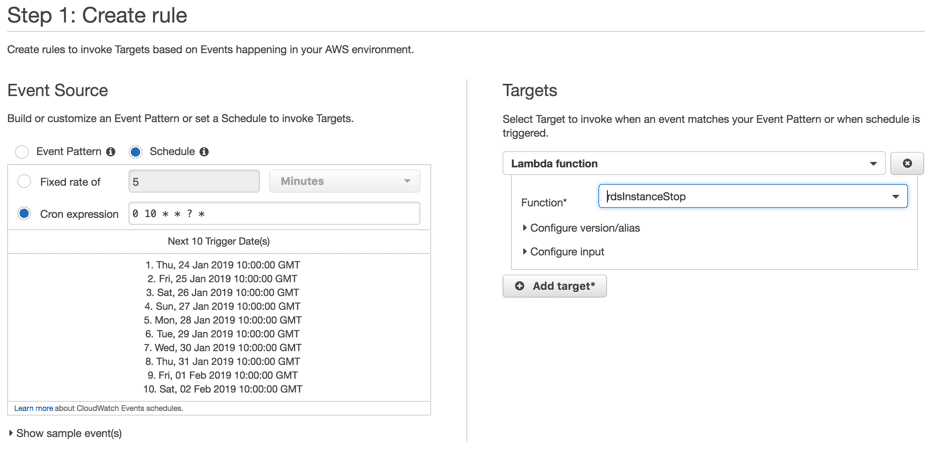
- Add the Lambda function we create previously as a target by clicking “Add target” and then click on “Configure details”
- Fill in the rule name ie. “stop rds” and the description
- Click Create rule
- After this, wait until 10 PM EST to see if the Lambda function gets triggered, this can be checked by going to the Cloud Watch Logs under the log group “/aws/lambda/rdsInstanceStop”
We hope this was helpful for you! Let us know if you have any issues or recommendations.